To address growing risks to defense suppliers (collectively the defense industrial base or DIB) due to malicious cyber activity, threat to intellectual property, economic espionage and data loss, the U.S. Department of Defense (DoD) is implementing enhanced requirements to protect sensitive data associated with DoD contracts. The Cybersecurity Maturity Model Certification (CMMC) program is applicable to all DoD prime and subcontractors. CMMC replaces the previous cybersecurity self-attestation to NIST 800-171 (technically by meeting DFARS Clause 252.204-7012) with a tougher third-party certification approach.
CMMC consists of 17 core security domains, and integrates various existing cybersecurity control standards into one unified standard for DoD contractors to demonstrate the maturity of their cybersecurity programs and practices.
The CMMC is more prescriptive and nuanced than other frameworks and standards. It will measure how well contractors and subcontractors in the defense supply chain have implemented and operationalized their cybersecurity practices and processes against a five-level maturity standard from Level 1 (basic cyber hygiene) to Level 5 (advance/progressive).
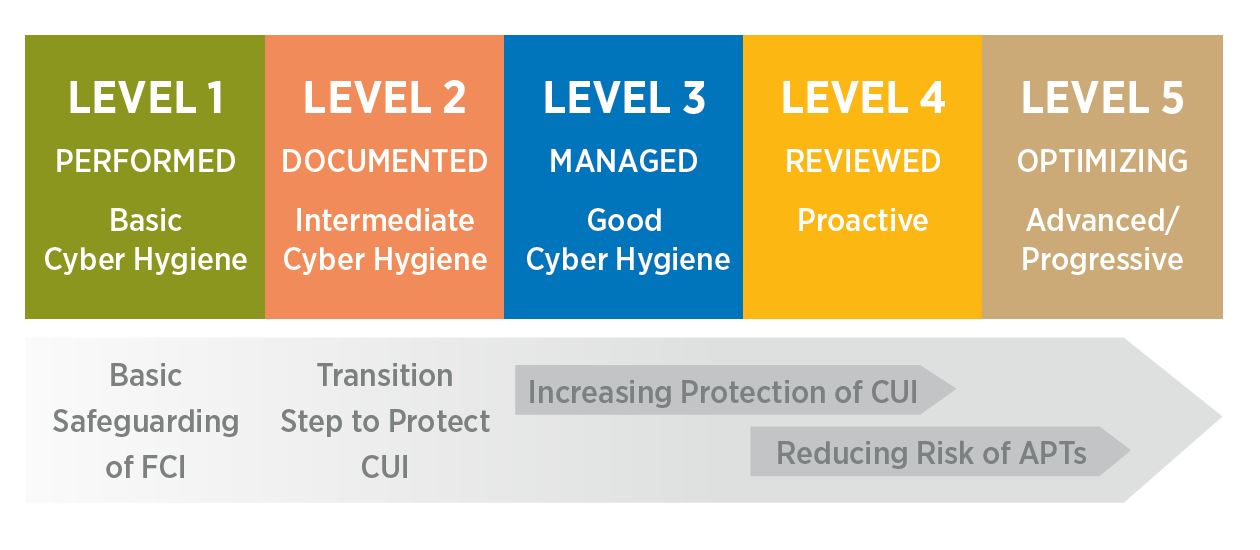
As the CMMC mandate moves through it early stage starting in June 2020 to its full implementation and enforcement in 2026, all DoD procurements (through requests for information [RFIs] and requests for proposals [RFP] will require one of the five maturity levels as a binary threshold for vendor participation. If Level 3 is the minimum level of maturity specified for an acquisition, for example, all vendors certified at Levels 1 and 2 will be ineligible to submit a proposal.
CMMC affects over 300,000 global providers of approximately $350 billion in goods and services procured by the Pentagon, whether they are large prime contractors or in the supply chain of another contractor.
The CMMC program materially raises the bar for the cybersecurity posture of suppliers, imposes formal certification of the maturity of their cybersecurity programs by independent third-party assessors and may lock companies into their initial certification level for an extended period that could impact defense vendors’ ability to participate in future Pentagon procurements.
“Companies that have already done their homework and invested in improving their cybersecurity risk have a step up on those that may be lagging in the maturity of their cybersecurity programs,” said Scott Corzine, a senior managing director at Ankura Consulting Group leading its CMMC initiative. “The DoD has given covered entities a reasonable window of time to move into compliance with the cyber maturity level required for the classes of products and service they may sell into the defense supply chain.”
Affected industry sectors
The DIB is a large network of companies across many product classifications, from obvious defense sector products like weapon and communication systems to less obvious products sold to the Pentagon, such as clothing, food or building materials. The multi-billion-dollar DIB includes manufacturers, systems integrators, service and technology providers, labs and research organizations, and other direct or indirect suppliers to the DoD.
“Every A.J. Gallagher client that sells directly into the Defense Department or may sell into a primary or secondary defense supplier should examine these relationships and determine, with the help of counsel, if they are likely to be entities covered by the CMMC program,” said John Farley, managing director of Gallagher’s Cyber Liability practice.
Some of the obvious sectors that may map to Gallagher’s industry practices include aviation/aerospace, electronics, communications, technology, logistics and maritime/marine. Other Gallagher clients may also determine that they indirectly participate in the DIB and should therefore explore preparing for a maturity certification. Some other industries that could potentially be impacted are construction and life sciences.
How the model works—what we know
On January 31, 2020, the DoD introduced version 1.0 of the CMMC that will wean direct and tangential defense suppliers from self-attestation of their cybersecurity posture using the NIST 800-171 standard. CMMC will require companies in the DIB to obtain a third-party certification of compliance and a maturity rating.
The process for securing that certification is being developed and managed by the CMMC Accreditation Body that will develop policy and have a professional staff to manage training and accreditation of certified third-party assessment organizations (C3PAOs). We are learning more about this body now that it has been formed and is being staffed and initiating its work.

The 17 CMMC cybersecurity domains (which map to several other security frameworks and standards that your organization may already align with) include:
- Access control
- Asset management
- Audit and accountability
- Awareness and training
- Configuration management
- Identification and authentication
- Incident response
- Maintenance
- Media protection
- Personnel security
- Process maturity
- Recovery
- Risk management
- Security assessment
- Situational awareness
- System and communications protection
- System and information integrity
Starting in June 2020 certain DoD requests for information (RFIs) will include a specific CMMC maturity level as an essential requirement for participation. Later in spring 2020, the DoD is expected to create a “marketplace” to help suppliers understand which CMMC maturity levels will be required for various product and service classifications and that may define how assessor companies become trained and accredited by the CMMC Accreditation Body to conduct CMMC certifications.
In October 2020, certain DoD requests for proposals (RFP) —in the missile defense space—will also begin requiring CMMC maturity thresholds. Other procurements will begin including CMMC requirements thereafter, until all DoD contracts include them
by 2026.
Not yet clarified are details like how defense suppliers can challenge assessment findings with which they may disagree, how they can dispute and appeal an assigned certification level, or how long it may take to re-assess for certification at a more mature rating.
What can Gallagher clients do now?
“Gallagher clients that directly or indirectly participate in the DIB and may be covered entities under the CMMC program should make these initial preparations,” added Mr. Farley:
- Consult with counsel to determine if your organization is likely to be affected by the CMMC program.
- Either internally assess the current state of your company’s cybersecurity program, capabilities and practices or engage a third-party expert firm to independently assess your security environment—ideally against the NIST 800-171 standard. This remains the optimal pro forma cybersecurity standard for indicating your potential gaps against the bulk of the CMMC requirements.
- Explore the gaps the company may have to the NIST 800-171 standard and begin to remediate those gaps. If your assessment reveals that your organization aligns with NIST 800-171, it may be close to achieving the CMMC Level 3, an excellent starting point.
These actions will inevitably improve the maturity of companies’ current cybersecurity posture as they get visibility into the current state of their programs, remediate gaps in their cybersecurity practices and processes, and prepare for independent assessment and certification against the CMMC.
The Recovery domain in CMMC includes maturity expectations around robust business continuity and disaster recovery planning. Aligning these plans with your business interruption and contingent business interruption coverages is an ideal approach. The Risk Management domain addresses the need to demonstrate a risk-based approach to cybersecurity. An Enterprise Risk Management (ERM) approach to identifying and remediating inherent cyber risks and transferring residual risks with cybersecurity, crime, property and D&O insurance would be helpful to improve CMMC maturity.
Inevitably, the cyber insurance underwriting community will begin to focus on compliance efforts to CMMC standards when evaluating risks. Explore with your Gallagher account team how early prophylactic cybersecurity efforts in these areas may put you in a more positive light as you navigate the cyber insurance market.
Ankura’s Scott Corzine added, “Do not delay this early assessment. Even though the contracts or subcontracts your organization has in the DIB may not require a CMMC certification until sometime between 2021 and 2026, it can reasonably take several years of security transformation to achieve confidence with your level of cyber maturity in anticipation of your formal maturity certification. Spreading the cost of remediation over several years is financially prudent, since preparation and compliance might entail new hiring, technology investments, and advanced training programs.”


