Author: John Farley

As the federal government continues to focus on cybersecurity issues and set the tone for heightened standards to defend against cyber threats, more and more industry sectors are feeling the effects. The Cybersecurity Maturity Model Certification ("CMMC") program is one such example, and one that Higher Education needs to pay attention to.
To address growing risks to defense suppliers (collectively the "Defense Industrial Base" or "DIB") due to malicious cyber activity, threat to intellectual property, economic espionage and data loss, the US Department of Defense (DoD) is implementing enhanced requirements to protect sensitive data associated with DoD contracts. It applies to all DoD prime- and sub-contractors, and cuts across a large network of companies and into many product classifications. This ranges from obvious defense sector products like weapon and communication systems to less obvious products sold to the Pentagon, such as clothing, food or building materials, as well as to manufacturers, systems integrators, service and technology providers. It applies to approximately 300,000 global providers of $264 billion in goods and services procured by the Pentagon, extending to labs and research centers that reside in the Higher Education sector.
The CMMC program materially raises the bar for Higher Education. It imposes a formal certification of the maturity of their cybersecurity programs by independent third-party assessors. Failure to meet CMMC standards could impact their ability to participate in future Pentagon procurements, jeopardizing critical government funded grants that schools rely upon.
CMMC Compliance Explained
CMMC replaces the previous cybersecurity self-attestation to NIST 800-171 with a tougher third-party certification approach. It consists of 17 core security domains and integrates various existing cybersecurity control standards into one unified standard for DoD contractors to demonstrate the maturity of their cybersecurity programs and practices.
The CMMC is more prescriptive and nuanced than other frameworks and standards. It will measure how well contractors and subcontractors in the defense supply chain have implemented and operationalized their cybersecurity practices and processes against a five-level maturity standard from Level 1 (Basic Cyber Hygiene) to Level 5 (Advance/Progressive):
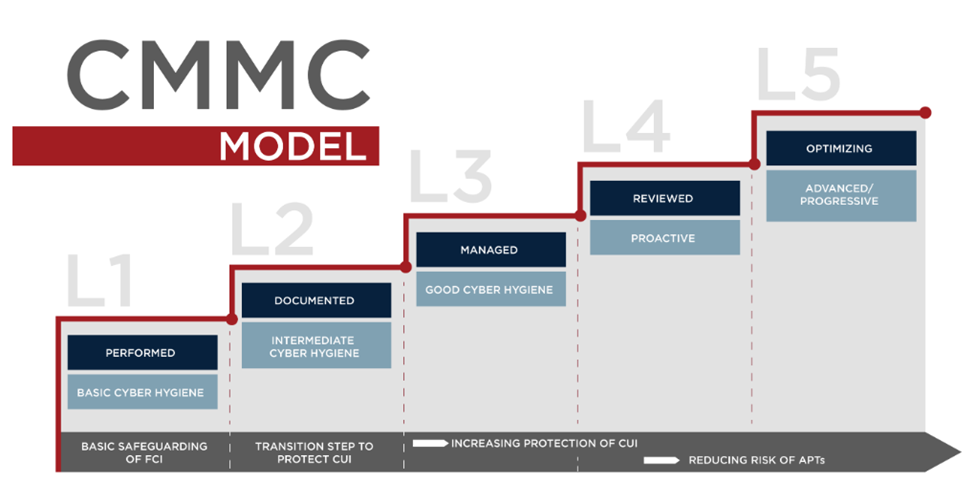
The CMMC mandate began in 2020 and moved through an early "demonstration” stage. It will progress to its full implementation and enforcement as late as 2025-2026. All Defense Department procurements (through RFIs and RFPs) will require one of the five maturity levels as a binary threshold for vendor participation. For example, if Level 3 is the minimum level of maturity is required, all vendors certified at Levels 1 and 2 will be ineligible to submit a proposal.
Areas of Focus
The 17 CMMC cybersecurity domains map to several other established security frameworks and standards, and include:

