Author: Joey Sylvester

- Defend critical infrastructure
- Disrupt and dismantle threat actors
- Shape market forces to drive security and resilience
- Invest in a resilient future
- Forge international partnerships to pursue shared goals
Defending critical infrastructure is of prime importance and, as such, is Pillar One, cementing that goal as the crucial factor in protecting the sectors from continued disruption by cyber threat actors.
What is critical infrastructure?
Executive Order 13636, issued in February 2013, defines critical infrastructure as assets so vital to our country that their loss or disruption would have significant consequences for our security, economy, and/or health and safety.2
Created in 2018, the Cybersecurity and Infrastructure Security Agency (CISA) is the chief federal agency tasked with the protection of US critical infrastructure. CISA oversees the protection of 16 sectors originally designated "critical" in Presidential Policy Directive-21 in February 2013:3
- Chemical
- Commercial facilities
- Communications
- Critical manufacturing
- Dams
- Defense industrial base
- Emergency services
- Energy
- Financial services
- Food and agriculture
- Government facilities
- Public health
- Information technology
- Nuclear reactors, materials and wastewater
- Transportation systems
- Water and wastewater systems
The National Cybersecurity Strategy lays bare the need for changes in how these critical sectors protect themselves from cyber attacks:
Market forces aren't enough. Continued disruptions of critical infrastructure and thefts of personal data make clear that market forces alone haven't been enough to drive broad adoption of best practices in cybersecurity and resilience.
In too many cases, organizations that choose not to invest in cybersecurity negatively and unfairly impact those that do, often disproportionately impacting small businesses and our most vulnerable communities. While market forces remain the first, best route to agile and effective innovation, they haven't adequately mobilized industry to prioritize our core economic and national security interests.
Voluntary efforts aren't enough. The American people must have confidence in the critical services underpinning their lives and the nation's economy. While voluntary approaches to critical infrastructure cybersecurity have produced meaningful improvements, the lack of mandatory requirements has resulted in inadequate and inconsistent outcomes.
Today's marketplace insufficiently rewards — and often disadvantages — the owners and operators of critical infrastructure who invest in proactive measures to prevent or mitigate the effects of cyber incidents.
Legislation is necessary. The Administration supports legislative efforts to impose robust, clear limits on the ability to collect, use, transfer and maintain personal data and to provide strong protections for sensitive data like geolocation and health information. This legislation should also set national requirements to secure personal data consistent with standards and guidelines developed by NIST. By providing privacy requirements that evolve with threats, the United States can pave the way for a more secure future.
In short, the US government has suggested that market forces and self-regulation have been inadequate in combating the continued threat of cyber attacks, and a lack of mandatory requirements or minimum standards hasn't been helpful in this fight.
Unfortunately, the stats support this assertion as critical infrastructure industries suffer higher data breach costs than other industries on average, as this graph from Cost of a Data Breach Report 2023 shows.4

National Cybersecurity Strategy Implementation Plan
In July 2023, the White House released the National Cybersecurity Strategy Implementation Plan.5 In this document, they operationalize the various goals set forth in the March 2023 document, with specific deliverables and timelines. For Pillar One — defend critical infrastructure — they have various initiatives related to targeting of critical infrastructure, specifically initiatives 1.1.2 and 1.1.3:
1.1.2: Set cybersecurity requirements across critical infrastructure sectors. The Federal Government will use existing authorities to set necessary cybersecurity requirements in critical sectors. Timeline for completion: 2Q 2025.
1.1.3: Increase agency use of frameworks and international standards to inform regulatory alignment. Regulations should be performance-based, leverage existing cybersecurity frameworks, voluntary consensus standards, and guidance — including CISA's Cybersecurity Performance Goals and the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity. Timeline for completion: 1Q 2025.
On other words, the US government will use existing authorities or create new authorities to mandate the adoption of the NIST Cybersecurity Framework (CSF) and CISA Cybersecurity Performance Goals (which align to NIST CSF) across the 16 critical sectors overseen by CISA.
Update on NIST CSF
The NIST CSF is currently nearing completion of the revision process.6 Version 2.0 is slated to be released following a period of public comment closing November 4, 2023, with a release of the final version scheduled for early 2024. CSF 2.0 encompasses 106 specific controls deemed necessary for cybersecurity protection across the major domains of Governance (new), Indentify, Protect, Detect, Respond and Recover. The specific requirements within the major domains are more granular and range from overall organizational context and strategy to regular security testing, access permissions, configuration management and more.
Until now, adoption of NIST CSF has been voluntary. With the release of these two documents, the US government is making the point that adoption won't be voluntary going forward. In fact, they're going to mandate the adoption of these frameworks across any organization operating within a critical sector, likely relying on the relevant Sector Risk Management Agency (SRMA) for enforcement.
Adopting the NIST framework and CISA's Cybersecurity Performance Goals (CPGs) at a high level can reduce the likelihood and impact of cyber attacks.7 Although the CPGs and frameworks go further in their requirements, common underwriting concerns such as multi-factor authentication (MFA), network segmentation, email security, incident response planning and others are all reflected, as well with specific recommended actions. In short, adopting NIST CSF and CISA CPGs can show a high level of cybersecurity maturity to underwriters during the insurance renewal process.
How do I get started?
Both NIST and CISA are ramping up efforts to provide resources and guidance on implementing these standards. The White House is also introducing ways to procure funding specific to Cybersecurity via the Federal grant process.8 Linked websites at the end of this article can provide a wealth of information.
Gallagher has a Cyber Risk Management team that knows these frameworks well and can support an audit of your cybersecurity programs focused on NIST CSF. Our consultants can help assess your current alignment with NIST CSF, determine any gaps between current controls or processes, and offer remediation guidance using our proprietary Gallagher Risk Management application.
The following are examples of reports from the Gallagher Risk Management Application.
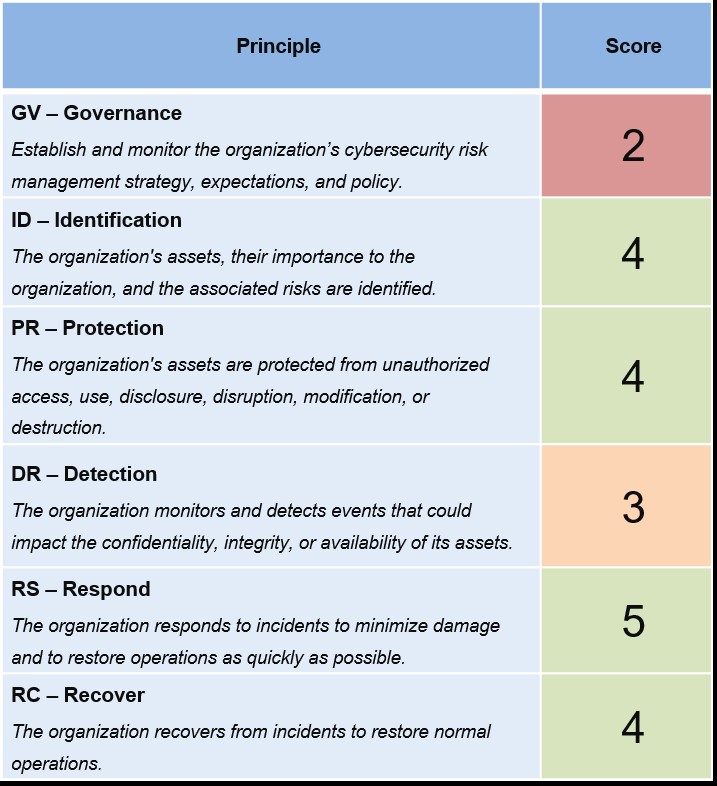
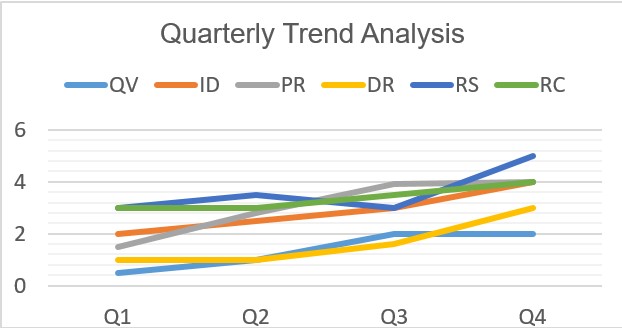

Additionally, the CPGs and CSF have many requirements our Cyber Risk Management team can help you address with the following bespoke services.
External and internal vulnerability scanning (CPG 1.E)
This continual service offered by the Cyber Risk Management team performs one scan each month. Our comprehensive report identifies which ports are susceptible to attack and the remediation steps required.
Ongoing vulnerability scanning against your publicly facing assets helps us identify potential vulnerabilities and exploits.
External, WLAN, WebApp, and Cloud penetration testing services (CPG 1.F)
A penetration test is an ethical hack of your network, to identify vulnerabilities and ultimately strengthen the security of your network.
Gallagher penetration testers can test internally and externally. External testing involves evaluating externally visible infrastructure, with the aim of gaining access. Internal testing mimics attacks behind a firewall, identifying how much damage could be done in the event of a breach.
Customized phishing simulations (CPG 1.F)
Phishing poses a real threat to your organization and your employees. A phishing email tries to obtain sensitive information from your employees such as login or bank account details and use this information to commit fraud, extortion and/or identity theft.
We recommend a multi-layered approach to phishing, in addition to cybersecurity awareness training, we offer a phishing simulation service that tests your employees' ability to identify and report phishing emails.
Responding to emails and clicking links is a huge part of the modern workplace. Spotting phishing emails is hard, and spear phishing emails are even harder to detect.
Performing phishing simulations helps ensure that the phishing risk is at the forefront of your employees' minds and enables your organization to assess how well your employees are helping to protect your business.
The phishing simulation itself comprises of an email campaign, undertaken over a period of three months, where users will be targeted and encouraged to click on links or open attachments.
Following each simulation exercise, we provide with a short report detailing what percentage of your workforce are cybersecurity aware and what percentage are vulnerable to a social engineering attack. The results give you the data you needs to determine whether your employees require further training in the following areas:
- Target users
- Deliver simulation
- Analysis and reporting
- Awareness and training
These simulations are aimed at changing your employees' behavior, so they can recognize, avoid and report potential threats that could compromise the critical business data and systems of your organization.
Pre-recorded or customized employee training solutions (CPG 2.I)
These hour-long sessions are delivered remotely to your staff members. They cover varying elements of cybercrime and how to stay vigilant against them.
Sessions cover a host of topics from the illegal sale of passports and guns on the dark web to ransomware and spyware.
We also have sessions focused on the cyber risks of working from home and to defend against common attacks.
Cyber Digital Roadmap Consultancy (CPG 2.P)
The Cyber Digital Roadmap Consultancy is a professional service in which a cyber consultant helps businesses design and implement a comprehensive digital security plan. With extensive experience in cybersecurity, risk management and IT strategy, our consultant works closely with your team to understand your unique needs and develop a roadmap to help safeguard your business from cyberthreats.
The service has two phases:
Discovery. A day to evaluate the current cyber security posture, which includes policies, procedures, network topology and systematic controls. This phase in conjunction with understanding the project parameters set within time, resources and budget.
Design. Plan and create a project roadmap focused on the Security by Design methodology. The project design demonstrates the change management required to architecture, infrastructure and process.
Incident management planning consultancy (CPG 2.S and 5.A)
Gallagher's Cyber Risk Management practice can review and create incident response processes for a wide range of potential incidents, including malware infection, phishing emails successfully exploiting a vulnerable target and many more. From simple checklists to detailed playbooks, we can create bespoke solutions based on your previous experiences and what we think you're most likely to face in the future.
There is a distinction between both incident management and incident recovery. Incident management sits within and across any response process, ensuring all stages are handled, including communications, media handling, escalations and any reporting issues. Incident response focuses on triage, in-depth analysis, technical recovery actions and more.
Our development process is centered on both the best practices discussed within the NIST Special Publication 800-61, and the tactics, techniques and procedures of adversaries identified by the MITRE ATT&CK® framework. We identify the most pertinent controls applicable to your organization and industry sector, and create a start to finish solution that prepares your organization.
In summary
Although we can perform an audit based on NIST CSF, we are also able to adapt to other frameworks as needed by a particular client or industry, such as NIST SP 800-53, ISO 27001 and SOC2, among others.
Implementing these frameworks and requirements may be a challenge for organizations whether they are critical infrastructure or not, and we are here to assist you in meeting these challenges head on.
For more information on any of these services or if you'd like to schedule a complimentary 30 minute consultation, contact us.


