
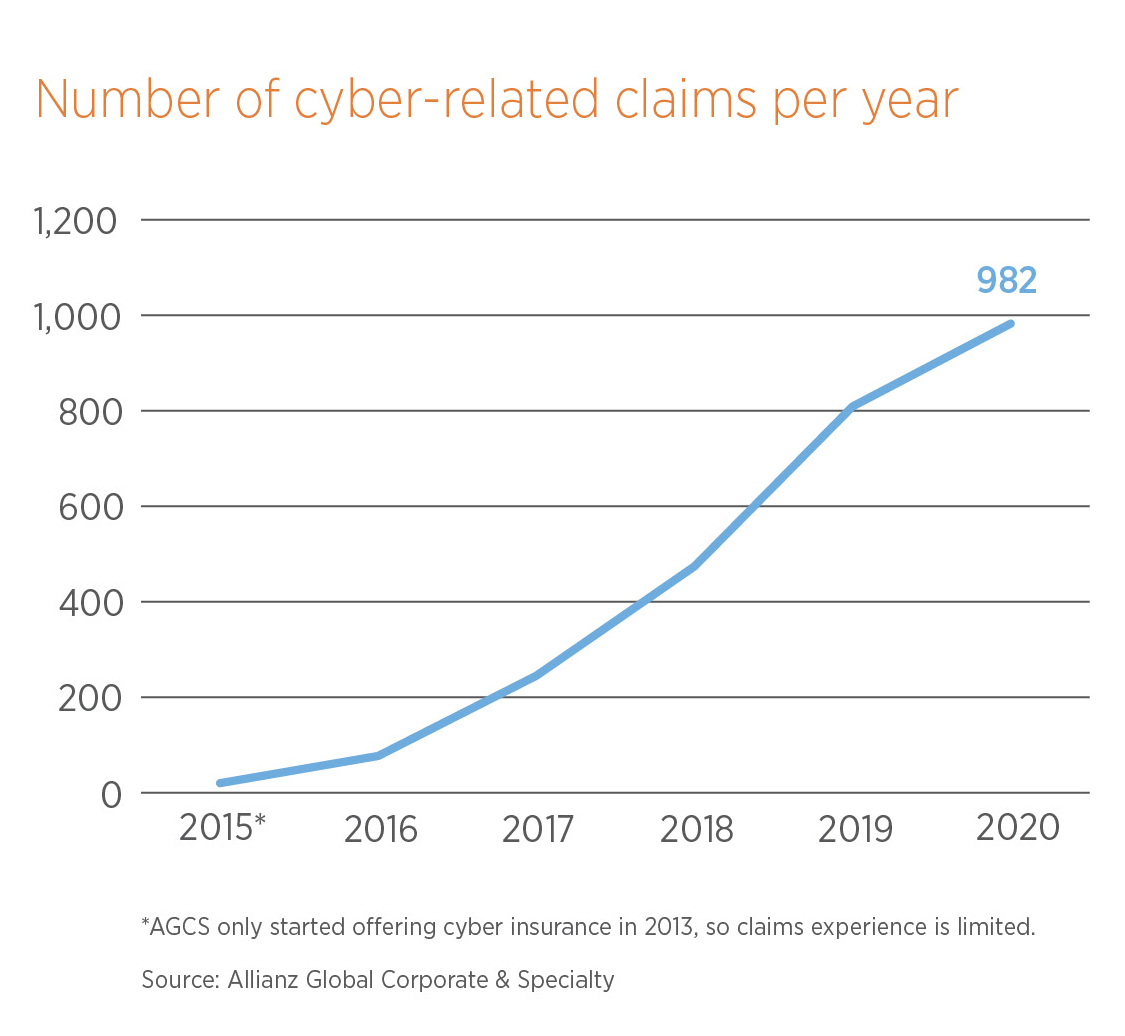
Why? Well the answer to that is simple. There has been a notable rise in cyber-driven claims in recent years, driven by the growth of the cyber insurance market but also by the rise in incidents such as data breaches, distributed denial of service attacks, phishing campaigns, and increasingly ransomware events which are becoming the dominant cause of losses, with 85% of all losses between 2015 and 2020 coming from ransom or other external hacks.1
Most insurers who underwrite cyber insurance are now requesting that businesses have Multi-Factor Authentication (MFA) for all remote access of their systems.
At Gallagher, we are seeing an increase in the number of businesses that are being refused cyber insurance cover due to a lack of MFA, leaving them exposed to significant losses.
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication (MFA) adds a layer of protection to the sign-in process. It strengthens security by requiring that users provide at least two pieces of evidence, or authentication factors, to prove their identity. By requiring multiple authentication factors, MFA provides a higher level of assurance about the user’s identity. Even if one of the factors has been compromised, the chances that all of the factors have been compromised are low.
MFA is enabled when at least two of the following categories of identification are used in order to successfully verify a user’s identity prior to granting access.
- Something You Know (A password)
- Something You Have (A mobile phone or a username)
- Something You Are (A device, biometric identification through a fingerprint or retina scan)

What should be protected with MFA?
Remote Network Access
MFA for remote network access is an important security control that can help reduce the potential for a network compromise caused by lost or stolen passwords. Without this control an intruder can gain access to a business network in a similar manner to an authorised user.
Privileged/Administrative Access
MFA for both remote and internal access to administrative accounts helps to prevent intruders that have compromised an internal system from elevating privileges and obtaining broader access to a compromised network. This can prevent an intruder from gaining the level of access necessary to successfully deploy ransomware across the network, erase activity logs, and create bogus user accounts or even turn off anti-malware protection.
Remote Access to Email
When accessing e-mail through a website or cloud-based service on non-corporate devices, MFA can help reduce an intruder’s ability to gain access to a user’s corporate email account. Threat actors often use email access to perpetrate various cybercrime schemes against businesses, as well as the businesses’ clients and customers.
For MFA to be fully effective, protection should extend to all employees, regardless of role.
Next Steps for Businesses
Providers in the MFA space are continually making the process easier, less expensive and more flexible for businesses to implement and users to access. Whilst MFA can be easy to use, applications that sit behind MFA are generally “cloud” based, so a lot will depend on the type of software and applications a business has and they should talk to their IT provider to have a holistic approach across their IT estate to implement MFA.
How Gallagher Can Support
Our dedicated Cyber Risk Management team can help you face the future with confidence by not only aiding you with reducing the likelihood of a breach, but also by giving you the tools you need to get back up and running with minimal damage if one does occur.
Our aim is to improve your cyber strategy, defences and ability to recover. We do this through the implementation of processes and procedures, such as the design of board level reporting templates.
We also help organisations gain information security standards such as Cyber Essentials, Cyber Essentials Plus and IASME Governance.
Why not request a 30 minute, free cyber risk management consultation? To find out more view our Cyber Risk Management page or speak to your Gallagher representative.
1. Managing the impact of increasing interconnectivity: trends in cyber risk allianz global corporate & specialty october 2020
The sole purpose of this article is to provide guidance on the issues covered. This article is not intended to give legal advice, and, accordingly, it should not be relied upon. It should not be regarded as a comprehensive statement of the law and/or market practice in this area. We make no claims as to the completeness or accuracy of the information contained herein or in the links which were live at the date of publication. You should not act upon (or should refrain from acting upon) information in this publication without first seeking specific legal and/or specialist advice. Arthur J. Gallagher Insurance Brokers Limited accepts no liability for any inaccuracy, omission or mistake in this publication, nor will we be responsible for any loss which may be suffered as a result of any person relying on the information contained herein.



